FortiGate firewalls are feature-rich appliances which can provide a range a functionality from end-user VPNs to switch and WLAN management. This makes them an interesting target for attackers. In this article, we will demonstrate how to extract credentials from a FortiGate backup file and how to properly secure your FortiGates to mitigate against this risk.
Backup File Encryption
When creating a backup of the configuration on a FortiGate firewall, you may optionally set an encryption password used to protect the entire configuration file. However, this is not required. Anytime the firmware version is updated via the web UI, an unencrypted configuration backup file is automatically created, at which point the browser will save the download locally to the administrator workstation. This configuration file could be a quick win for an attacker who gains a low-privileged initial foothold on the workstation.
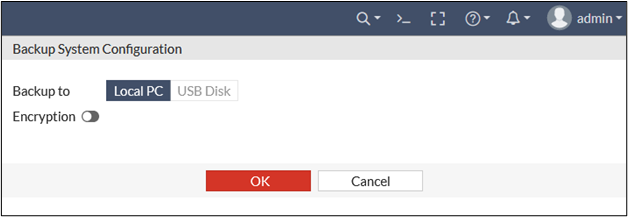
One reason this is interesting to an attacker is that the configuration file naturally contains detailed information about the network, ACLs, and more. Another reason is that the configuration file contains various sorts of credentials. While at a glance these credentials appear to be encrypted in the configuration backup file even when an encryption password has not been set, they are quite trivial to decrypt.
Credential Encryption
The FortiGate, and thus its configuration backup file, stores many different types of credentials. None of these credentials are stored in the backup file in plaintext, even when an encryption password is not used to encrypt the entire file. However, not all credential types are protected in the same manner. Some credentials such as administrative account passwords are hashed, but many others are encrypted using AES and as such are reversible.
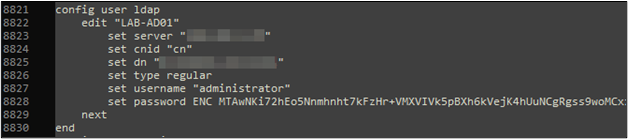
By default, the key used to encrypt these credentials is a static/hardcoded value. Various tools now exist to decrypt these credentials, or you could read up on some of the reversing done by various researchers in this area and write your own.
Decrypting “All the Things”
Now let us see what kinds of credentials we can decrypt from a plaintext configuration backup of our FortiGate using the default hardcoded AES key!
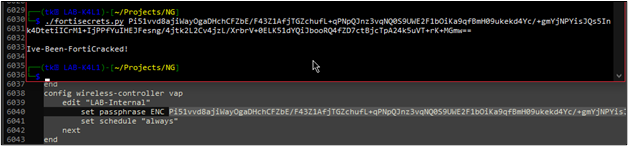
Overall, we were able to successfully decrypt the below credential types to recover the plaintext values.
- Wi-Fi PSKs
- VPN PSKs
- Local VPN user passwords
- LDAP user passwords
- RADIUS shared secrets
- SNMPv3 passwords and keys
Mitigation
To protect your FortiGate config backups from prying eyes, you should always ensure you set an encryption password to protect the entire file. As an added layer of protection, you can run the commands below on your FortiGates to set a custom AES key used to protect credentials within your configuration backup files just in case an unencrypted backup is inadvertently created, or to protect the unencrypted backups created automatically during firmware updates.
config system global
set private-data-encryption enable
end
Written By:
 Jeremy Burroughs is an Offensive Security Consultant at Netragard working on a variety of assessments and projects including penetration testing engagements and team toolkit development.
Jeremy Burroughs is an Offensive Security Consultant at Netragard working on a variety of assessments and projects including penetration testing engagements and team toolkit development.
With over 10 years of professional experience in IT and cybersecurity…>>Read Bio






