Hack of the Month: January 2024
Cyberattacks and data breaches are a daily occurrence, often due to common vulnerabilities such as insecure default configurations or weak passwords. However, in this Hack of the Month series, we’ll be exploring cyberattacks that break the mold, using novel vulnerabilities and exploitation techniques.
The January 2024 Hack of the Month focuses on the Ivanti vulnerabilities that prompted the Cybersecurity and Information Security Agency (CISA) to issue multiple emergency directives resulting in government agencies being instructed to disconnect the affected systems (Ivanti Connect Secure, Ivanti Policy Secure, and ZTA Gateways) by midnight on February 2nd.
The original directive addressed two initial vulnerabilities discovered in December 2023, and then the updated directive addressed an additional vulnerability found in February 2024.
The Origin Story of Five Ivanti Vulnerabilities
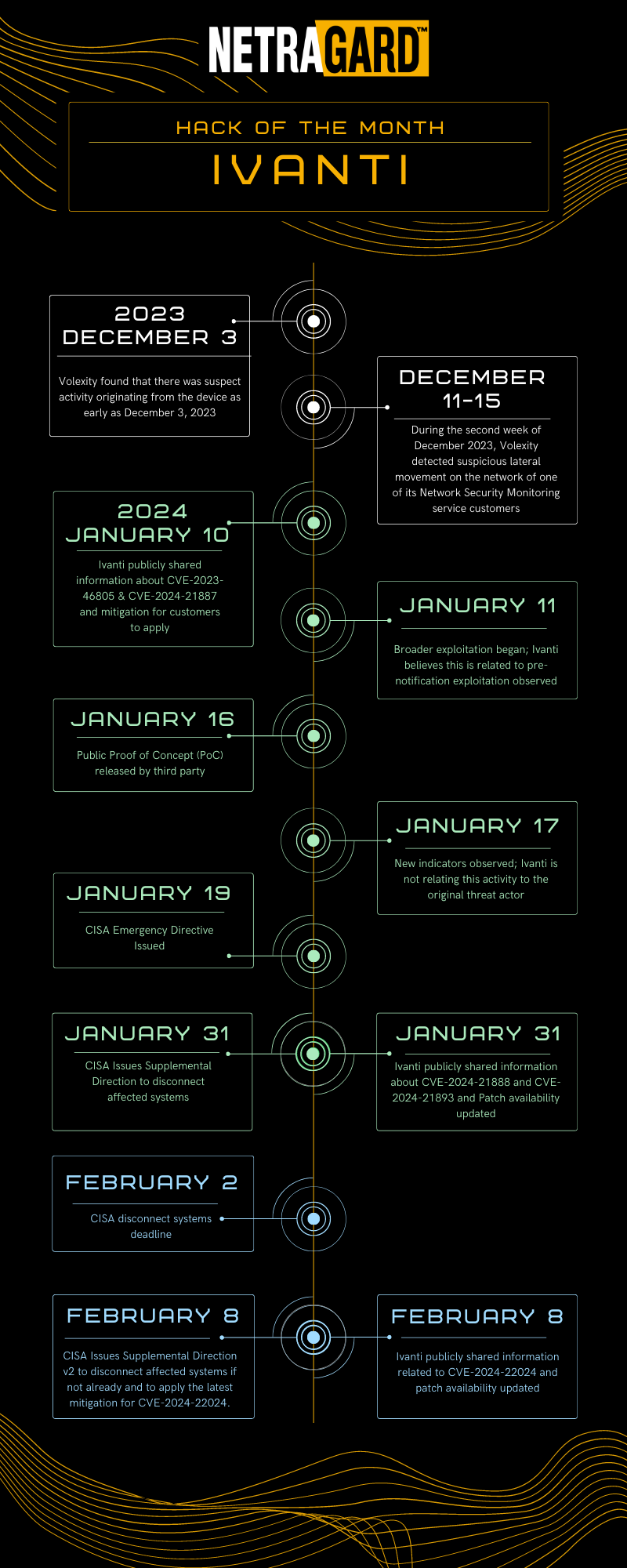
In December 2023, Volexity detected suspicious activity on the network of one of its customers. During the incident investigation, they were able to trace the malicious activities back to the customer’s Internet-facing Ivanti Connect Secure (ICS) VPN appliance where they discovered the attackers were using two zero-day exploits to compromise the device.
By chaining these two vulnerabilities together, the attackers were able to bypass access controls to gain admin-level permissions (CVE-2023-46805). Then, as an authenticated admin, the attackers exploited a second vulnerability (CVE-2024-21887) allowing them to execute arbitrary commands on the vulnerable Ivanti system.
Once the attackers had full control of the Ivanti device, they were able to modify the JavaScript of the VPN Login page and record the credentials of anyone who connected. This allowed the attackers to move laterally within the client’s environment and steal sensitive information, backups, and additional credentials. Volexity worked with Ivanti and Mandiant to confirm the findings and, on January 10th, Ivanti publicly disclosed the CVE-2023-46805 and CVE-2024-21887 vulnerabilities.
As Ivanti continued their investigation, they discovered two more vulnerabilities that they disclosed on January 31st, 2024, the same day Mandiant released a report attributing the initial attacks to a China-nexus espionage threat actor. According to Ivanti, these vulnerabilities impacted “a small number of customers”, and included a server-side request forgery (SSRF) vulnerability that allows an attacker to access certain restricted resources without authentication (CVE-2024-21893), and then another privilege escalation vulnerability (CVE-2024-21888) which allows an attacker to elevate privileges to that of an administrator. These vulnerabilities — and the threat that they posed — inspired CISA’s follow-up directive to immediately take affected systems offline and begin threat hunting for potential intrusions.
Shortly thereafter, a fifth major vulnerability (CVE-2024-22024) was announced on February 8th, which allows for an attacker to access certain restricted resources without authentication. While Ivanti is currently working on patches for all affected versions, they have provided workaround mitigations via an XML configuration file as well as guidance on indicators of compromise, though they found no evidence of the vulnerability being exploited in the wild.
Timeline:
What’s the Risk?
The Ivanti vulnerabilities have been actively exploited since early December, and the newly discovered ones make them even more dangerous. Due to the large number of versions affected by these vulnerabilities, Ivanti has had to triage the release of patches, prioritizing those versions that have the highest number of installs according to their internal telemetry tools. In addition, the official recommendation is to completely wipe and reset the Ivanti device before applying the patches and mitigations as the attackers may have a backdoor into the system that would allow for an attacker to have persistent access even after the vulnerability is mitigated.
Netragard recommends following the CISA directive (even if your company is privately owned) which instructs government agencies to disconnect devices until they have been factory reset and patched. For more information on how to reset and update your Ivanti device please follow Ivanti’s instructions which can be found here and here.
Preventing These Attacks
In total, an estimated 7,000 devices were vulnerable to exploitation on January 15, 2024. Of these, attackers compromised an estimated 1,700. While we wish we could tell you that there is a simple way to prevent attacks like this from happening, the honest truth is there isn’t. Zero-days and vulnerabilities are always going to be a part of any internet-connected network, which is why we at Netragard are strong proponents of the “Defense in Depth” model and the “Assume Breach” mentality. The goal should be to layer tools and processes for better security that can help you identify and mitigate a threat before it becomes damaging.
This is where penetration testing really shines. It helps organizations evaluate their security posture and readiness against such threats, while taking proactive measures to strengthen their defenses. Penetration testing can also help identify better ways to detect and respond to novel vulnerabilities, exploitation techniques, and zero-day attacks. Netragard and our Real Time Dynamic Testing™ methodology were derived from vulnerability research & exploit development practices which enable our testers to be uniquely skilled at understanding what vulnerabilities attackers are searching for and exploiting in their hacks – We Protect You From People Like Us!
To learn more about protecting your company from the latest and greatest threats, contact us.






