Real Time Dynamic Testing™ (RTDT) is an advanced penetration testing methodology developed by Netragard, designed to provide a comprehensive assessment of applications, systems, or entire organizations. Named for its dynamic, research-driven approach, RTDT is highly extensible and incorporates key components from established frameworks like OWASP and OSSTMM. Unlike traditional methodologies, RTDT emphases a focus on the discovery of both known and novel vulnerabilities to ensure maximum testing depth and coverage.
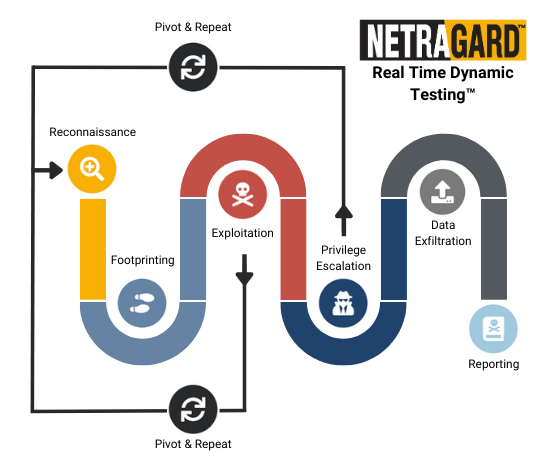
Real Time Dynamic Testing™ involves testing an application or service in real-time by using various penetration testing techniques to identify vulnerabilities and weaknesses that could be exploited by attackers. The testing is conducted remotely, and the tester interacts with the application, service, and its users to simulate a real-world attack scenario. This methodology is highly extensible and often incorporates components from the OWASP, the OSSTMM, bleeding edge offensive tactics, and our internal vulnerability and Zero Day research.
This methodology typically includes the following steps:
The tester collects information about the target application or service, such as its infrastructure, user base, and technologies used.
The tester identifies potential vulnerabilities and attack vectors, such as open ports, weak passwords, and outdated software.
The tester attempts to exploit identified vulnerabilities, such as SQL injection or cross-site scripting, to gain access to sensitive data or take control of the application or service.
The tester attempts to escalate privileges to gain further access to the application or the underlying infrastructure.
The tester attempts to leverage the compromised system and data to move to new systems on the network, repeating steps 1 – 5, to gain complete control over a company’s sensitive information and critical systems.
The tester attempts to identify sensitive information to mimic real threat actors and perform exfiltration of mock data to determine the efficacy of detection capabilities.
The tester provides regular updates to the client as well as a comprehensive and customized report (at the end of the engagement) detailing the Path(s) to Compromise, identified vulnerabilities, and suggested remediations to enable our clients to deploy effective defenses that detect and prevent active breaches from becoming damaging.
Real Time Dynamic Testing™ is designed to provide a more accurate and realistic assessment of an application or system’s security posture than traditional penetration testing methods. By simulating a real-world attack scenario, the methodology can identify vulnerabilities and risks that may be missed by other types of testing. Additionally, because the testing is conducted in real-time, it can provide immediate feedback to developers and stakeholders, allowing them to take action to address vulnerabilities and improve the overall security of the systems and applications.

Netragard offers an extensive range of professional services and a high degree of specialization. We serve both private & public sectors. We bring over 15 years of experience.