Ready to see how your security stands up to a real hacker’s curiosity? At Netragard, we don’t just do a basic scan and call it a day – we launch real-world attacks to expose your riskiest gaps and hand you a prioritized fix list that actually fits your business. We blend custom tools with business logic, help you breeze through compliance, and circle back with a free retest to make sure your remediations actually work. In our world, “secure” means tested, proven, and ready for anything.
Think your perimeter can handle what the bad guys throw at it?
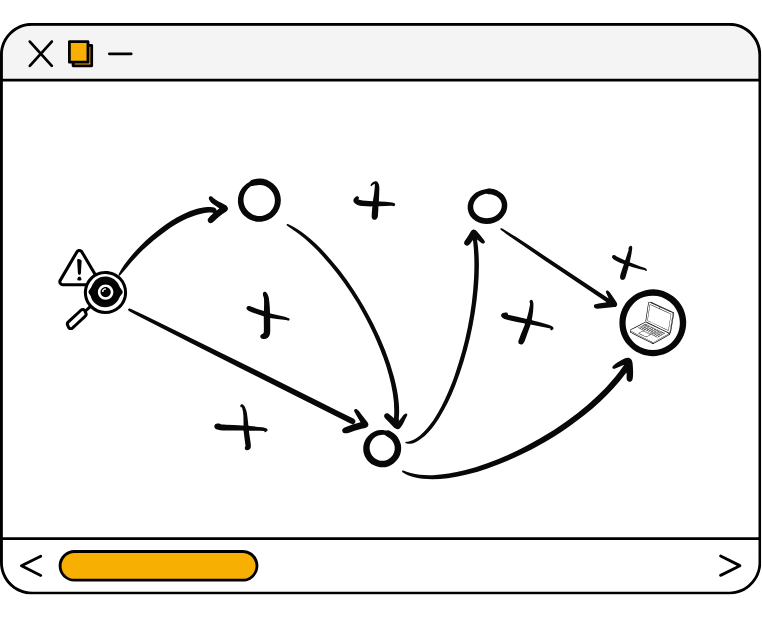
How does your internal network stand up to someone already on the inside?
Confident your WiFi isn’t giving an attacker a shortcut into your environment?
It’s not a bug, it’s a feature. Perfect! That’s just hacker-speak for ‘exploit me.’
App store ready? Great. How does it survive a real-world jailbreak?
Most staff can dodge the obvious scam, but can they spot the phish crafted just for them?
Keycards, cameras, and guards? Awesome. We’ll just blend in with the maintenance crew and see how far we get.
Enjoying the cloud’s sunny forecast? Let’s make sure you’re not about to get caught in a downpour of risks with our cloud security assessment services.
Need security advice that actually fits your business? Let’s turn strategy into your strongest defense with our advisory and consulting services.
We tailor every engagement—whether it’s IT due diligence, IoT assessments, or policy reviews—to match your unique goals, industry, and risk appetite.
Our experts think like hackers, delivering clear guidance on everything from OSINT and breach exposure to configuration hardening and executive threat mapping.
Whether you’re launching a new product, navigating a merger, or just want peace of mind, we partner with you to elevate your security posture and keep your business a step ahead.
Netragard offers an extensive range of professional services and a high degree of specialization. We serve both private and public companies.
A Silver Level Penetration Test is consistent with industry standard penetration testing services. The Silver Level relies on automated vulnerability scanning with manual testing to discover common vulnerabilities.
A Gold Level Penetration Test ensures advanced technical depth and coverage for network connected devices and web applications using our proprietary Real Time Dynamic Testing™ methodology.
A Platinum Level Penetration Test provides maximum testing depth and coverage, exceeding what one would experience in a real-world threat. We use a variety of custom tools and techniques such as Real Time Dynamic Testing™, pseudo malware, social engineering and more.
Real Time Dynamic Testing™ is an advanced penetration testing methodology that is unique to Netragard and derived from vulnerability research & exploit development practices.
The methodology is highly extensible and often incorporates components from the OWASP, the OSSTMM, bleeding edge offensive tactics, and more. Real Time Dynamic Testing™ can be delivered entirely without automated vulnerability scanning.
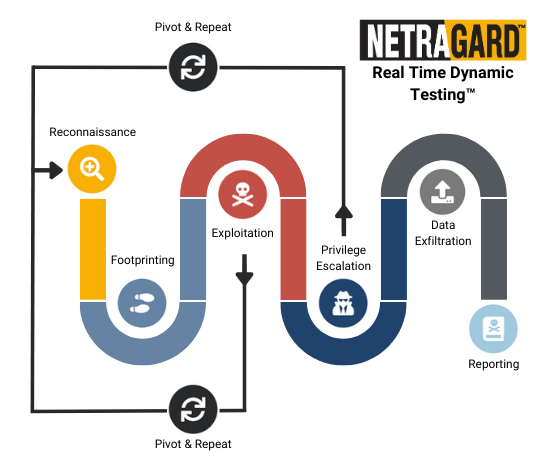
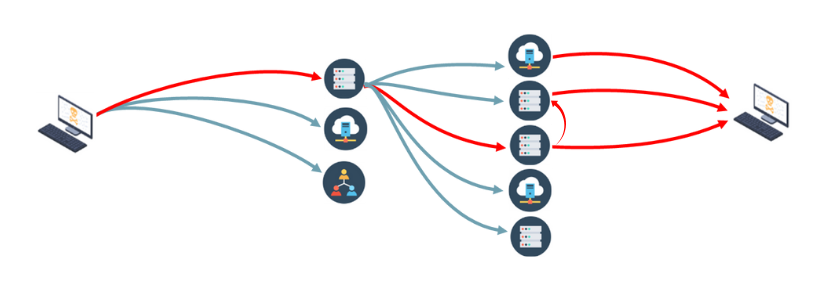
The Path to Compromise is the path that an attacker takes to move laterally and/or vertically from an initial point of breach to areas where sensitive data can be accessed.
Understanding the Path to Compromise enables organizations to deploy effective defenses that detect and prevent active breaches from becoming damaging.
All customers who undergo a penetration test with us have the opportunity to earn a Certificate of Security if they successfully resolve all identified issues regardless of severity within a 60 day window.

Netragard offers an extensive range of professional services and a high degree of specialization. We serve both private & public sectors. We bring over 15 years of experience.