Overview
Netragard was engaged by a midsized HR company to assist in their internal incident response process when they detected activity resulting in changes to customer payroll accounts. This case study emphasizes the importance of early incident detection and response through a well-considered plan. Additionally, it demonstrates the benefits of having a third-party on retainer to help mitigate the damages when an attacker targets you or your clientele.
Initial Detection
The HR company’s internal systems had detected that 30 client accounts had their payroll banking information changed from similar IP addresses. This was unusual because this was across their client base, so it was unlikely that these IPs would be attributed to all these individuals in various locations, industries, and time zones. While most compromised accounts did not have multi-factor authentication (MFA) enabled, accounts with additional security leveraging SMS codes were also affected.
Since this suspicious activity was only limited to a handful of users and the changes originated from IPs outside of the organization, it was unclear how these accounts were being targeted and compromised. Was this a standard phishing campaign used against their clients? If so, was there a data leak with their client list or was this a typical account takeover when individuals use the same password across multiple sites and those credentials are released on the dark web after a data breach? It was essential to identify the method of attack to execute a defensive strategy.
Identifying the Attack Vector
Netragard performed Open-Source Intelligence (OSINT) research against the IP addresses assumed to be malicious with the objective of collecting information about the threat actor and their respective infrastructure. OSINT is the process of discovering publicly available information that could be used by attackers to hack an organization. This includes reviewing social networks for key employees, discovering leaked or stolen records (usernames, passwords, financial data, etc.), darknet research, and registration data for domain names.
Each malicious IP traced back to devices located in the United States, many of which were traditional home networking devices like your typical home Wi-Fi router. These home networking devices had not been updated or patched in years, connected directly to the internet, and were easy targets for the hackers to compromise and use as a proxy. This technique is often used by criminals to hide their true source and allows the attacker to bypass conditional controls related to geolocation when the attacker is in another country.
While most of the IP’s led to dead ends, a recently registered “lookalike” website domain was identified as a perfect clone of the legitimate HR website. A “lookalike” domain is a domain that is slightly altered with the intent to deceive. An example of this would be an attacker registering a domain like “myhrapp[.]us[.]com” or “mylrrapp[.]com” when the legitimate domain is actually “myhrapp[.]com”
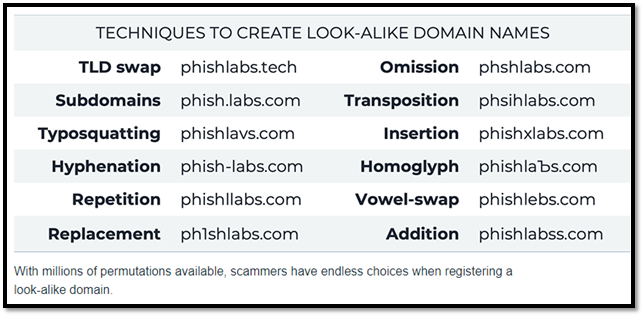
Figure 1. Lookalike domains example (Phishlabs)
This fake website was also linked to an active Google Ads campaign and the source of the compromised accounts.
Malicious Google Ads
Google Ads are paid online advertisements presented to a user when they type in certain keyword(s) in the search field of their internet browser. These advertisements are shown to the user at the top of the search results in a section tagged as “Ad” or “Sponsored.” These keyword “Ads” can be purchased by anyone in a bidding process like an eBay auction and the attackers had successfully bid on and won the Google Ad placement for the HR website’s name.
The Google Ad campaign tricked users into thinking they were clicking on the HR website by getting their fake website listed at the top of the search page ABOVE the legitimate HR website. When users googled the company name to reach the HR login page (instead of typing the URL directly in the browser) the attacker’s fake website came up first with an exact clone of the legitimate website. Most recently, a similar attack targeted users of the Notepad++ software and the following image is an example of an attack involving a malicious Google Ad for Webex.
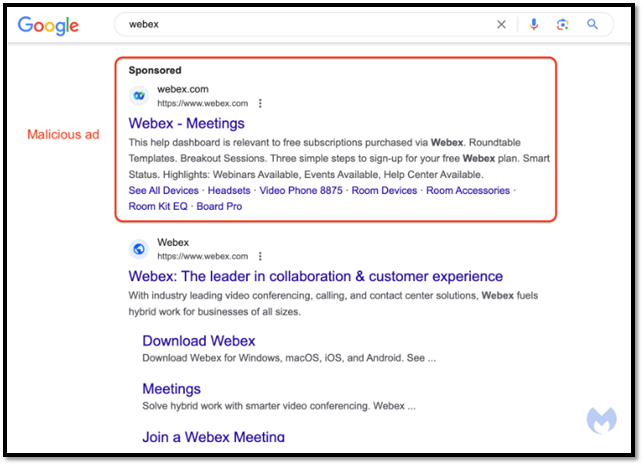
Figure 2. Malicious Google Ad Example (Malwarebytes)
Upon visiting the website, victims unknowingly had their credentials stolen via the fake login page. The credentials were then forwarded in real time to the attacker who attempted to authenticate to HR company’s website. If the login failed, the attacker would cause an error message to be displayed on the fake website requesting credentials again. If authentication was successful but MFA was encountered, the attacker would cause the fake website to request the victims MFA token. Once the attacker successfully accessed the HR company’s website, they promptly modified the victim’s banking details to transfer funds to the attacker’s own bank account.
Now with full understanding of the attack chain, the team was able to act in conjunction with the Legal Team. They reached out to the hosting providers to take down the fraudulent web sites, domains, and reported the malicious ads to Google. Each time a malicious website and domain was taken down, the attackers would quickly (sometimes within minutes) set up another website clone on another lookalike domain while enabling another Google Ad campaign in five separate instances.
Hacking Back – Grey Area
While the HR’s Legal team was working to take down the fraudulent domains and malicious ads, Netragard was digging into the code of the fake HR website and found a hard coded API (Application Programming Interface) key. This API key linked to a cloud publish-subscribe (pub/sub) event messaging service. As mentioned earlier, this allowed the attackers to receive the stolen credentials (and MFA codes) from the victim and then attempt to authenticate in real-time.
Upon review of the pricing tiers for this cloud pub/sub messaging service, there was a free tier that allowed 100 events per day. The Netragard team built a quick script to call the hardcoded API multiple times to force it to reach its daily service quota. This disabled the use of the platform until the quota was reset either manually by forcing the attacker to pay for additional “events” or to wait until the quota was reset the next day. This helped buy time for our client’s IT and Legal teams to execute the takedown requests with both Google and the domain registrars while also preventing additional customers from becoming victims of the malicious website. Netragard prides itself on staying up to date on the latest research for both offensive and defensive techniques, hence our slogan, we protect you from people like us.
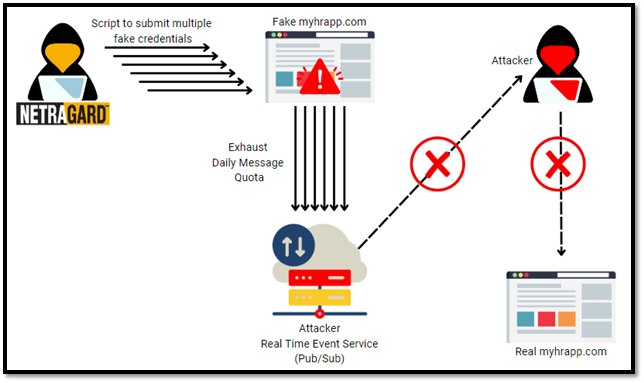
Figure 3. Hacking Back – Netragard, We Protect You from People Like Us.
Key Takeaways
This was an interesting and unique engagement because the IT maturity and detection skills of the HR organization are far above the industry average. They invested heavily in their incident detection and response capabilities. The early detection and speed of their response mitigated any damage that might have otherwise been realized from the fraudulent banking activity, and they protected their clients. They were also proactive and engaged a third-party firm to help investigate and validate their findings along the way.
Based on Netragard’s observations, the attackers exhibited a high degree of sophistication and appeared to be well financed. Their approach involved the use of innovative methods to establish credible Google Ad campaigns and redirected victims to malicious landing pages. They also used novel techniques to bypass multi-factor authentication and responded to takedowns by quickly setting up new paid campaigns on newly purchased domains. While the HR company did an excellent job of handling this incident there is always room to improve. Here are the key takeaways to improve the security posture at your organization:
- Web Navigation & Site Verification
- Make it a habit when visiting websites, especially those from google ads, to double check the URL for anomalies.
- Always exercise caution when interacting with any website, especially those associated with sensitive information.
- Monitor for Lookalike domains
- Use third-party services like ZeroFox, Terbium, Recorded Future, or Allure Security to monitor for doppelganger domains. Alternatively, consider using a self-hosted monitoring solution like DNSTwist or Cert.sh API.
- Use app based Multi-Factor Authentication (MFA) solutions:
- Many text (SMS) MFA solutions have the codes valid for 10 minutes whereas app-based MFA codes are only valid for 30 seconds.
- Leverage dynamic blacklists
- Use third-party IP reputation services to maintain a dynamic blacklist of known-to-be-hostile IP addresses.
- Leverage tools like GreyNoise and DarkOwl to investigate IP addresses
- Resource: https://socradar.io/the-ultimate-list-of-free-and-open-source-threat-intelligence-feeds/
- Muti-level approval for significant changes
- When significant changes are made to sensitive data, require secondary approvals. For example, changes to financial information, contact information, security questions, etc.
- Automated Authentication Defenses
- Implement application logic that automatically locks accounts after multiple failures from the same IP addresses are detected.
- Impossible Travel
- Identify and block login activities from multiple geographically distant locations within specified short time period.
- Incident Detection & Response
- Design an effective incident response policy and test the policy regularly by leveraging advanced penetration tests.
- Have a third-party security firm on retainer for incident response.






