By now, most everyone has heard of the SolarWinds breach. Cybercriminals took advantage of SolarWinds’ poor cybersecurity practices to gain access to their network and implant malicious code within updates to their Orion network monitoring solution.
This Orion solution is widely used, and its compromise led to the attackers gaining access to the networks of many large enterprises and a significant percentage of US government agencies. As a result, intellectual property and sensitive government data has been compromised and much of it is being sold online. Investigations into the incident are still ongoing.
SolarWinds and SOX Disclosures
The SolarWinds breach has likely caused significant damage to the organization reputationally and financially. The damage caused by SolarWinds’ negligence is widespread, and the company will likely be the defendant in numerous lawsuits regarding the breach.
A recent class action lawsuit filed against the company’s leadership by SolarWinds shareholders demonstrates the potentially far-reaching impacts of such a breach. As a publicly-traded company, SolarWinds is subject to the Sarbanes-Oxley Act (SOX), which was passed in response to the Enron scandal to protect investors. Under SOX, a company’s CEO and CFO must sign an attestation that publicly-released statements regarding the company’s financial status are correct.
The lawsuit against SolarWinds focuses on a statement in SolarWinds’ 2019 10-K filing that acknowledges the risk of cyberattacks to the company. Based on this statement, the company acknowledges that this risk exists, that steps should be taken to mitigate this risk, and that any breach should be reported to shareholders.
SolarWinds was initially breached on September 4th, 2019, but the breach was not reported until December of the next year. Since the company has filed multiple 10-Q statements since with no reference to the breach, the plaintiffs in the SOX case allege that SolarWinds was negligent in managing its cybersecurity risk. Additionally, investigation into the incident revealed other instances of cybersecurity negligence, such as the use of a password solarwinds123 on the SolarWinds update server.
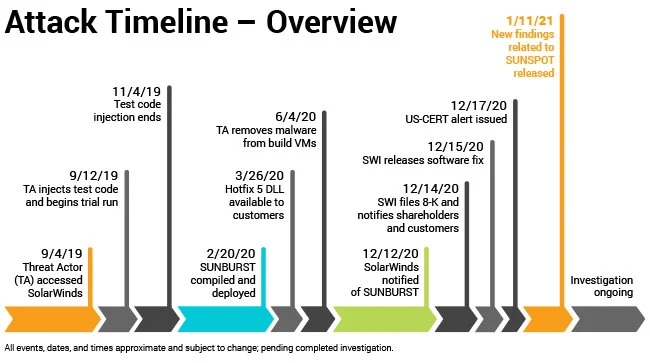
Source: Solarwinds
SOX Disclosures and the Cost of Poor Cybersecurity Due Diligence
Obviously, SolarWinds’ CEO and CFO are not directly responsible for detecting and remediating security incidents within their organization. However, they do hold overall responsibility, and the SOX Act allows them to be held personally responsible for misleading or false statements within SOX disclosures.
Any organization can suffer a security breach, but it is the responsibility of a company’s leadership to ensure that due diligence is performed to prevent incidents like the SolarWinds breach. SolarWinds failed to do their due diligence in two crucial ways:
- Internal Cybersecurity Failures: As SolarWinds mentions in their 10-K, it is impossible to fully protect against cybersecurity threats. However, the company failed to follow even the most basic cybersecurity best practices as demonstrated by the use of a blatantly insecure password (solarwinds123) on its update server.
- Failure to Perform Proper Security Testing: Passing a Penetration Test is not proof of strong cybersecurity, as demonstrated by Trustwave’s certification of Target before the 2013 breach. However, a Penetration Test should have detected the use of such a weak password on the update server. This oversight demonstrates a failure to perform proper due diligence on behalf of both SolarWinds and any organization that performed a Penetration Test for the company.
Taking Responsibility for Corporate Cybersecurity
The class action lawsuit against SolarWinds – if successful – creates a strong precedent for holding corporate executives personally responsible for their companies’ security failures. Under the SOX Act, executives can face 10 years in prison and a $1 million fine for signing off on misleading statements, and 20 years and $5 million if the deception was willful.
In cybersecurity, as in any field, mistakes can be made, and companies can be breached despite their best efforts. However, making a “good faith” effort toward strong corporate cybersecurity – including contracting regular Penetration Tests by a competent testing firm – is essential to earning forgiveness for cybersecurity failures. The appearance of good security isn’t the same as the real thing.






