Thanks to whistleblower Peter McIndoe and the enlightened members of the Birds Aren’t Real movement, we now know the truth… Beginning in the late 1950s, the United States government exterminated over 12 billion birds. Today, the “birds” you see resting on power lines are actually federal surveillance drones, disguised with feathers and beaks, charging their batteries before the next mission.
While the Birds Aren’t Real movement is, in fact, not real and rather an elaborate social experiment – intelligence agencies have been inspired by nature on multiple occasions when designing gadgets for clandestine espionage operations. Commonly seen animals, such as birds, are innocuous and unlikely to draw attention, making them strategically advantageous by hiding in plain sight.
The U.S. Central Intelligence Agency (CIA), for instance, has developed and deployed multiple animal-based intelligence gathering devices over the years. During the Cold War, the agency attached lightweight cameras to harnesses and used pigeons as aerial spies to take photographs of their targets. Even a cat, equipped with a microphone and transmitter, was field tested in the hope it could be used to eavesdrop on the conversations of foreign adversaries. Agent Acoustikitty was its callsign.
A Malicious Mallard
The Hak5 USB Rubber Ducky is neither made of rubber nor is it a duck. Instead, this device is just a normal USB flash drive… in appearance. It can still act as a storage device, but the Rubber Ducky stores payloads and exfiltrated victim data rather than the usual family vacation photos.
When plugged into a computer, it assumes the role of a “peripheral” device. Though you may be unfamiliar with the terminology, you have almost certainly used these devices before. Normal mice, keyboards, webcams, printers, and speakers are all examples of peripheral devices that provide input or output over wired or wireless connections to a computer.
The vulnerability that the Rubber Ducky exploits is the implicit level of trust that is given to computer peripherals. Connections demonstrate user intent, as they require physical access to the computer in order to make wired connections or configure Bluetooth settings. If a connection is made, it is assumed to be intentional. We all know what they say about making assumptions.
A Rubber Ducky, when inserted into a USB port on the target machine, takes advantage of this trust by emulating a keyboard. Using payload scripts, sequences of keystrokes and shortcuts are sent to carry out actions on the target machine. This attack vector, known as keystroke injection, was introduced along with the debut of Hak5’s malicious tool back in 2010.

DuckyScript
The payload scripts used by Rubber Ducky are written in a programming language called DuckyScript. In DuckyScript 1.0, the entire language only consisted of three commands.
In its current version (3.0), it is feature rich and supports fundamental programming constructs including: comments, constants, variables, functions, loops, if/else statements, conditional statements, and operators.
DuckyScript can even be used to emulate mouse movements to navigate to different positions on a screen via cursor keys.
Device specific commands allow you to programmatically control the Rubber Ducky’s execution state. When the device is in standby, it is referred to as being in “arming mode”. While executing a payload, it is considered to be in “attack mode”, which can be initiated using the ATTACKMODE command. There are a variety of both required and optional ATTACKMODE parameters that will determine the state of functionality and identity of the device.
To allow for sufficient execution time, scripts can be stalled using the DELAY command. However, hardcoded wait periods result in a cadence that is easily discernable from legitimate end user typing – which can be detectable. To appear more natural, the inclusion of the $_JITTER_ENABLED directive with its value set to TRUE will generate random delays in between every keystroke within the script.
Hak5 even showcases community submitted payload scripts in an official repository, the Payload Hub. The featured payloads consist of everything from pranks (like playing a song on Spotify) to exploits with serious security implications (such as exfiltrating sensitive data to remote servers).
A Discount Ducky
A major selling point of Hak5’s Rubber Ducky is its ease of use thanks to the intuitive DuckyScript language. Additionally, it looks just like any other USB drive, so it won’t sound any alarms. However, with a little know-how, some C++, and an hour of your time – you can also emulate a peripheral device and use your own custom case to blend into the environment.
ESP32
The ESP32 is a versatile and cost-effective series of microcontroller chips designed and manufactured by Expressif Systems. These chips are widely used in Internet of Things (IoT) devices due to their built-in Wi-Fi and Bluetooth capabilities. The ESP32’s popularity has led to its integration into various development boards, including those produced by Arduino, a well-known open-source electronics company.
Arduino has leveraged the ESP32’s capabilities by incorporating it into their own line of boards, such as the Nano ESP32. To complement these hardware offerings, Arduino provides user-friendly software tools that simplify the process of programming and controlling ESP32-based devices. This combination of affordable hardware and accessible software has made the ESP32 an attractive option for both hobbyists and professionals working on IoT projects.
Teensy
Another, low-cost microcontroller with a small footprint is the Teensy. In fact, this was the core component for Netragard’s own version of USB espionage, the PRION Mouse. Netragard created this for a penetration testing engagement with strict limitations where the target had a single IP address bound to a firewall and strict restrictions and controls were in place for social engineering and physical access.
The PRION device was a USB mouse that disguised the teensy microcontroller, a micro-USB hub, a micro flash drive, and custom malware. The mouse was carefully disassembled and modified to accommodate these additional components while maintaining its original appearance and functionality – increasing the likelihood of it being used by unsuspecting targets.
The mouse was packaged as a promotional item and then shipped to a carefully selected employee of the target company. Once plugged in, the mouse functioned normally while covertly executing Netragard’s custom malware, which then established a connection back to our attacker’s system, allowing for full network compromise.


A Zoo’s Worth + Some
The concept of disguised hacking tools extends beyond USB drives. Although other Hak5 devices adhere to the animal kingdom naming convention, not all do, nor are they duck related. However, there are some worth mentioning:
The Screen Crab
The Hak5 Screen Crab is a discreet device designed for covert video surveillance. This innovative tool functions as an intermediary between HDMI-connected devices, such as computers and monitors or gaming consoles and TVs. Its primary purpose is to capture screenshots or record video content without detection. It can be particularly useful for those who need to monitor or document on-screen activities without interfering with the target system’s operation.

The storage capacity is determined by the SD card used, and with support for SD Extended Capacity (SDXC) cards, the Screen Crab can save a vast number of images. Storage can also be rotated, where the oldest files are overwritten first allowing the device to be left in place for extended periods of time.
This tool is ready to use straight out-of-the-box, though by making changes to a configuration file, you can customize its operation:
LED ON
CAPTURE_MODE IMAGE
CAPTURE_INTERVAL 5
STORAGE FILL
BUTTON EJECT
WIFI_SSID name
WIFI_PASS password
If the Screen Crab is connected to Wi-Fi, the screen captures can even be viewed remotely via Hak5’s Cloud C2.
The O.MG Cable
In 2013, the German magazine DER SPIEGEL published a series of articles discussing the Tailored Access Operations (TAO) division – an elite hacking unit of the U.S. National Security Agency (NSA). One of the articles featured leaked documents, marked as TOP SECRET in classification. The documents were pages of the Advanced/Access Network Technology (ANT) catalog, which revealed hacking tools available to the TAO unit.
The Hak5 O.MG Cable, developed by Mike Grover, is the civilian equivalent of one of the leaked tools, the Cottonmouth-I.
The O.MG Cable looks just like any ordinary charging cable: USB-A or USB-C, with either C, Lightning or Micro ends, and available in both white and black. In its dormant state, it also behaves as an ordinary cable would, providing data transfer and 5V charging. However, within the housing of the USB end, is an antenna, microcontroller, and concealed storage chip. The cable is usually leveraged to execute payloads on mobile devices.
The cable is Wi-Fi capable and can connect to an existing Wi-Fi network or it can generate its own wireless access point and serve an administrative webpage. With the Elite model, the O.MG cable can reach out to a remote server over an encrypted connection, allowing you to control it from anywhere.
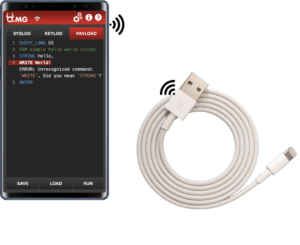
Both the Basic and Elite models can carry out keystroke and mouse injection attacks using the same DuckyScript language as the Rubber Ducky. The Elite model is also able to log keystrokes. Both models come with the Geo-Fencing and Self-Destruct features. Geo-Fencing can be used to maintain a dormant state until a certain network is detected, while Self-Destruct has two different options to wipe the O.MG cable if it leaves the vicinity of a certain network.
With the HIDX StealthLink feature available only to the Elite model, remote shells and exfiltration is possible even on air-gapped machines. You can even add a remote server instance.
National Rubber Ducky Day: More Than Just Bath Toys
These tools, once the domain of shadowy government agencies, are now accessible to the public. While they offer red team members new avenues for testing security, they also serve as a stark reminder of the potential threats lurking in everyday objects.
As we observe National Rubber Ducky Day, it’s crucial to remember that in the realm of cybersecurity, appearances can be deceiving. The next time you find a stray USB drive or charging cable, think twice before plugging it in – it might be more than meets the eye.






