Hollywood has always had their creative takes on hacking in movies and TV shows, ranging from random concepts pulled out of thin air to almost fully realistic hacking scenes. In this blog, we’re going to evaluate techniques from classic hacking movies and shows that are still relevant today.
Sneakers: Physical Red Teaming
Sneakers (1992) is a movie about a group of hackers who are hired to steal a code breaking device that could decrypt anything in the world. The movie starts with a scene where a team of hackers are hired to break into a bank and do so by transferring funds out of a bank account via physical access to a workstation terminal.

The Sneakers first send a teammate underground near an unsecured cable box near the bank dressed as a tradesperson to manipulate the phone cables to tap the phone lines and set off the fire alarm. Under panic, the guard in charge scrambles to report the fire alarm over the telephone while the hackers sneak into the building. Bishop, one of the team, then jumps on an unsecured workstation and withdraws money from an account.
The team of penetration testers (which was not a well known term when the movie was made) also employed techniques such as wiretapping and person-in-the-middle (PITM) on the security guard’s phone line, telling him to not worry about the false alarm. Although we’ve mostly phased out old-school telephone lines, they are still in use in at many hotels and hospitals, and unencrypted Voice-over-IP (VoIP) calls using SIP and RTP are still prevalent and hackable.

Physical red teaming, like the heist in the start of Sneakers, is very much still done today with financial institutions being frequent clients of physical security tests due the sensitive nature of on-premise assets (computers, but of course also cash in vaults). Social engineering, impersonation, wiretapping, and physical access to corporate workstations are all still part of the arsenal of physical red teamers today.
The Girl with the Dragon Tattoo: Hardware Implants
Another classic hacking movie is The Girl with the Dragon Tattoo (2011). It’s based on a thrilling book by the same name written in 2005 by Stieg Larsson, where the skilled hacker and orphan Lisbeth Salander was hired to investigate the disappearance of a person forty years ago. The book was even included in the Ohio State University’s famous Cybersecurity Canon.
There were a few exciting hacks in the movie, but early on Lisbeth employs various techniques to break into a building and plant a physical hacking device in the service cabinet where the network switches and phone lines were. Let’s see what she does.

First, she stands outside of the target apartment building out of sight while someone punches in the passcode to access the building. Since each number makes a unique sound on the number pad, she was able to deduce the passcode, and quickly entered the building to perform reconnaissance in its service area. She took photos of the servers, network switches and cables, notes on the wall, and so on.

Then later, she comes back with a prepared backdoor device. It’s not explained to the audience what it was, but it looks like a Nokia N900, which runs a Linux operating system. Back in the day, the N900 was a popular target of installation of a system called “PwnPhone“, a Linux distribution bundled with many open source and proprietary hacking tools.
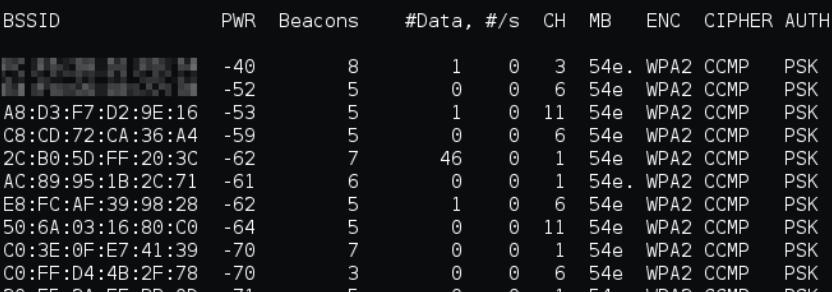
The screen of the phone seems to be running something akin to airodump-ng from the Aircrack-ng suite, which is used for sniffing nearby WiFi networks. The device she placed had an antenna on it which looks like a WiFi antenna. She also plugs what seems to be an ethernet cable into the cabinet at the end, so that she has access to the network of the building. This type of physical device backdoor / implant is still very commonly used in real world penetration testing today, sometimes known as a “drop box” or “drop device”. It’s usually a very small device (such as a Raspberry Pi) and has both wired and wireless network capabilities, much like Lisbeth’s pwnphone. It can provide remote access to the wired LAN (Local Area Network), attack the network to obtain credentials (through tools such as Responder), as well as attack nearby wireless access points.
Matrix Reloaded: Port Scanning and SSH Hacking

Next, we have Matrix: Reloaded (2003), a famous sci-fi movie in the Matrix series. Aside from being the source of the popular matrix-style screen with raining green text widely shown on hacker desktop backgrounds worldwide, it’s also home to one of the first realistic hacking scenes in a movie. In a hacking scene, Trinity uses the famous port scanner Nmap to scan a target host. Upon discovering the SSH port, she then proceeds to use an exploit called “sshnuke” which pertains to a SSHv1 CRC32 vulnerability to gain access to the system. It’s been reported that the author of nmap “almost danced” in the movie theater when he realized they featured the tool.
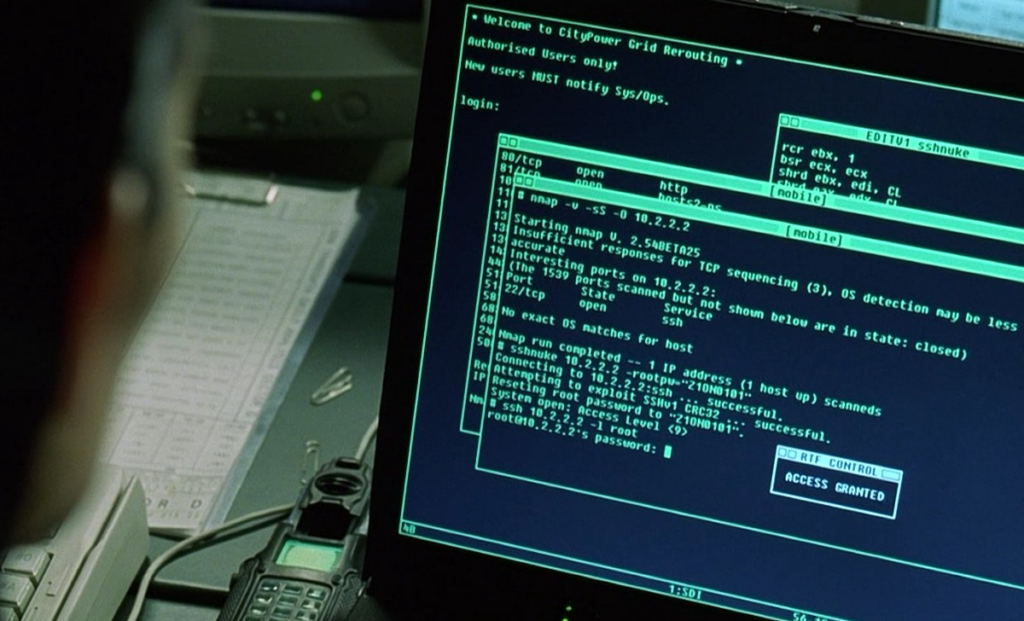
Port scanning, and in this case, TCP SYN scanning, is one of the most widely used techniques of network reconnaissance. In the screenshot you can see the -sS parameter used, which is SYN scanning in nmap; it’s the act of sending TCP SYN packets (the start of a TCP handshake) to many ports on a network host to discover which one is open based on the response. After finding the open port 22 with the service SSH on it (which stands for Secure Shell, a remote access protocol), she uses an exploit that attacks SSHv1 CRC32 to achieve full remote access to the system (a.k.a Remote Code Execution, or RCE), then changes the root password to login.
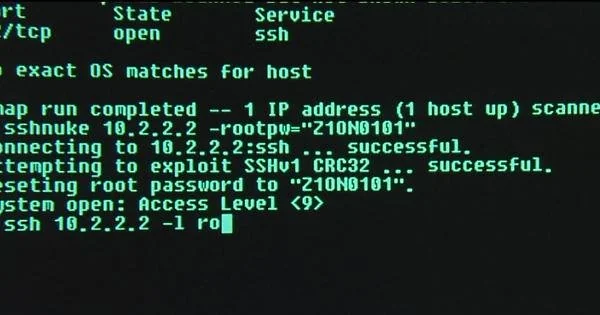
The vulnerability, which most likely is a reference to CVE-2001-0144, is an integer overflow vulnerability which can be triggered remotely by exploiting a bug in the SSH CRC32 attack detection code. The attack is described by a CERT Coordination Center bulletin here:
“By sending a crafted SSH1 packet to an affected host, an attacker can cause the SSH daemon to create a hash table with a size of zero. When the detection function then attempts to hash values into the null-sized hash table, these values can be used to modify the return address of the function call, thus causing the program to execute arbitrary code with the privileges of the SSH daemon, typically root.”
Today, port scanning and SSH hacking is still very prevalent. Port scanning tools like nmap are frequently used by penetration testers to scan external as well as internal networks for open services they can exploit. Most of the time, SSH attacks come from automated botnets that bruteforce passwords, since SSH vulnerabilities are much fewer and further in between, as OpenSSH is a very well-audited piece of software. However, recently another scary SSH RCE vulnerability came into light (CVE-2024-6387), where a researcher was able to exploit a regression of an old vulnerability’s patch to gain full code execution as root on 32-bit Linux systems. The actual attack, luckily, takes a long time to execute (from hours to days), not nearly as instant as the one in the Matrix movie. You can read more about the latest SSH vulnerability and how to mitigate it on our blog here.
Mr. Robot: Password Cracking and Social Engineering
Finally, we have the USA Network television series Mr. Robot (2015). Without spoiling too much, this series follows a hacker vigilante determined to take down a giant corporation using his hacking skillset. The production is supported by a team of experienced technical advisors, including Michael Bazzell, ensuring an authentic portrayal of the cyber-security world. With its meticulous attention to detail, Mr. Robot offers a treasure trove of realistic hacking scenes that closely mirror real-world Tactics, Techniques, and Procedures (TTPs). Each scene is carefully crafted to showcase genuine commands, tools, and techniques, delivering a level of authenticity that Hollywood has rarely achieved before.
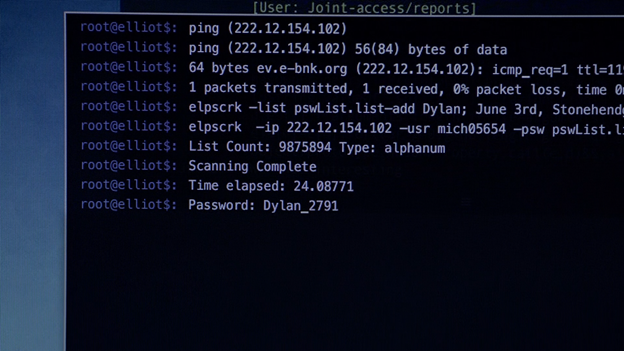
In the first episode, we see Elliot using a tool called elpscrck, presumably short for “Elliot’s Password Cracker.” While this tool is likely fictional, it seems to emulate a custom wrapper script designed to streamline traditional password-cracking techniques, such as leveraging custom wordlists. A wrapper script is a lightweight program which can automate the execution of multiple tools. As we watch the screen, Elliot begins to narrate, “Hacking her was simple. Her password, Dylan_2791. Favorite artist and the year in which she was born, backwards.” We see Elliot using personal information which he has gathered, and used it to generate a custom password wordlist, which is used to successfully crack the password.
In another scene, we watch as another character is provided a Rubber Ducky and instructions on how to use it once they infiltrate a building.

“This is a Rubber Ducky. All else fails, you find an FBI laptop anywhere on the floor, they’re usually Panasonic Toughbooks, [and] plug this guy in. Wait 15 seconds, then yank it. Next to a tool with Mimikatz, it will pull all cached passwords and domain info in and save them on this.”
Similar to the well-known tool Mimikatz, this USB device from Hak5 is a real security tool, designed to resemble an ordinary flash drive. However, under the hood, this device operates as a keyboard which enables users to inject pre-programmed keystrokes stored as scripts, allowing them to download files, steal passwords, execute commands, or launch malicious programs.
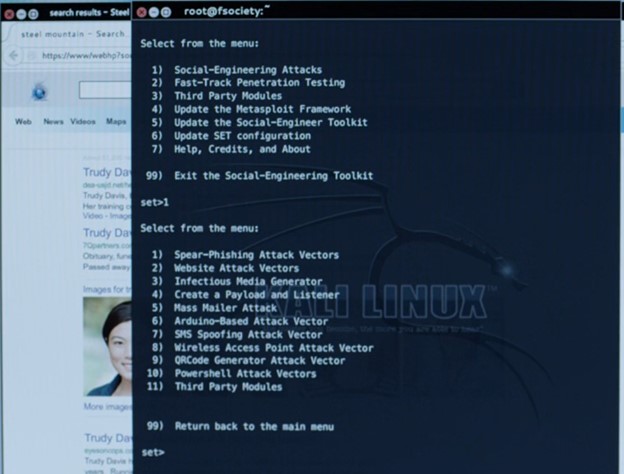
In one of the many episodes featuring Social Engineering, we watch as hackers hover over their laptop and begin to configure the Social Engineering Toolkit (SET). As the suspense builds, the hackers race against time to target an employee escorting Elliot out of a building. They quickly launch the SET program and send a fake family emergency SMS text message to the employee, effectively distracting them and giving Elliot the crucial opportunity to escape. This is a real and well-known tool, which aided many users in their social engineering engagements.
Mr. Robot is filled with scenes that highlight RFID spoofing, car hacking relay attacks, and a variety of social engineering scenarios, making it a must-watch for cybersecurity and hacking culture enthusiasts. The series is not only entertaining, but also pays a genuine tribute to the hacking world by meticulously focusing on these details and incorporating credible technical dialogue, far beyond the typical buzzwords often seen in other hacker films.
Conclusion
Although many movies and tv shows have unrealistic hacking scenes, many techniques employed by these fictional hackers are inspired by real world techniques and exploits. Sometimes, working in penetration testing can be a bit like hacking in the movies (check out our case studies for real world examples), and many cyber professionals were once youngsters inspired by these scenes to get into security. If you end up watching (or re-watching) any of these hacking movies and feel inspired to hire someone to break into your company, feel free to contact us and request a quote!






