Earlier this morning one of our more savvy customers received an email from [email protected]. The email contained a “New Message Received” notification allegedly sourced from CEO Tom Morgan. Contained in the email was a link that read, “Click here to sign in and read your messages”. Fortunately we had already provided training to this particular customer that covered Social Engineering and Phishing threats. So, rather than click on the link they forwarded the email to Netragard’s Special Project Team, which is like throwing meat to the wolves. The actual email is provided below in figure 1.
Figure 1
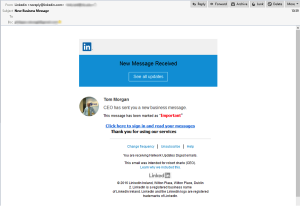
The first step in learning about who was behind this threat was to follow the “click here” link. The link was shortened using the URL shortener ow.ly and so we used curl to expand it. While we were hopeful that the URL would deliver some sort of awesome zeroday or malware, it didn’t. Instead it served up a fake LinkedIn page (Figure 2) designed to steal login and password information.
Figure 2

The server hosting the phishing site was located in Lebanon and of course was not maintained or patched properly. Quick reconnaissance showed that directory listing was enabled, that the server was using an outdated and very exploitable version of cPanel, and that the server had been breached by at least four other parties (there were at least 4 backdoors installed). We used one of the backdoors to gain access to the system in the hopes of learning more (Figure 3).
Figure 3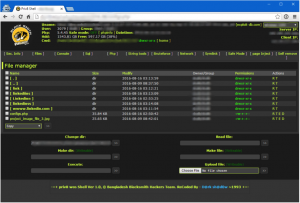
Our team quickly zeroed in on the “linkd.php” file that was used to generate the phishing page shown in Figure 2. We explored the file looking for information related to where stolen passwords were being kept. Initially we expected to see the passwords logged to a text file but later found that they were being emailed to an external Gmail account. We also looked for anything that might provide us with information about who was being targeted with this attack but didn’t find much on the system.
We were able to identify the victims of the campaign by making hidden modifications to the attackers phishing platform. These modifications allowed us to track who submitted their credentials to the phishing site. When studying the submission data it quickly became apparent that the attackers were almost exclusively targeting Luxembourg based email addresses (.lu TLD’s) and were having a disturbingly high degree of success. Given that people often reuse passwords in multiple locations this campaign significantly increased the level of risk faced by organizations that employ the victims. More directly, chances are high that organizations will be breached using the stolen passwords.
The LinkedIn campaign was hardly the only campaign being launched from the server. Other campaigns were identified that included but may not be limited to DHL, Google, Yahoo and DropBox. The DropBox campaign was by far the most technically advanced. It leveraged blacklisting to avoid serving the phishing content to Netcraft, Kaspersky, BitDefender, Fortinet, Google, McAfee, AlienVault, Avira, AVG, ESET, Doctor Web, Panda, Symantec, and more. In addition to the blacklisting it used an external proxy checker to ensure page uptime.
Finally, we tracked the IP addresses that were connecting to the system’s various backdoor. Those IP addresses all geolocated to Nigeria and are unfortunately dynamic.
Summary
This phishing campaign highlights two specific issues that can both be countered with careful planning. The first is that employees are easy to phish especially when they are outside of the office and not protected by spam filters. This is problematic because employees often reuse the same passwords at work as they do outside of work. So stealing a LinkedIn password often provides attackers with access to other more sensitive resources which can quickly result in a damaging breach and access to an organizations critical assets. The solution to this issue is reasonably simple. Employees should be required to undergo regular training for various aspects of security including but not limited Social Engineering and Phishing. Second, Employers should require employees to use password management tools similar to 1Password. Using password management tools properly will eliminate password reuse and significantly mitigate the potential damages associated with password theft.
As for our Nigerian friends, they won’t be operating much longer.






