Attackers might be relentless, but your security strategy doesn’t have to run on caffeine and chaos. Netragard’s Penetration Testing and Security Advisory Services help you cut through the noise and see your environment through a hacker’s eyes – spilling the details that would make you the talk of breach forums, before it becomes tomorrow’s headline. You’ll get actionable insights that not only keep adversaries guessing, but also check every compliance box along the way.

Our team thinks like the adversary, using custom tools, zero-day expertise, and hands-on tactics to map out exactly how attackers could compromise your environment. We’ll show you the real paths to compromise, highlight what’s working, and hand you a plan to disrupt attacks before they start – so you’re ready for whatever the bad guys throw at you.
We don’t just hand you a laundry list of vulnerabilities. Our reports deliver prioritized, impact-based remediations with clear guidance and supporting links, so you know exactly where to focus for maximum risk reduction. We factor in your business logic, threat landscape, and use research-driven methods – so you’re not patching fluff while the real threats sneak by.

Need to check those SOC 2, PCI, FINRA, or other regulatory compliance boxes? We’ve got you covered with executive summaries, letters of attestation, and certificates of security – plus a free retest so you can prove you’ve actually locked things down. Auditors and regulators will love you, and you’ll have real peace of mind to back it up.
Netragard offers an extensive range of professional cybersecurity services and a high degree of specialization. For two decades we’ve protected organizations across Banking, Finance, Healthcare, Software, and other critical industries.
Penetration Testing Services enable organizations to identify and resolve vulnerabilities in their IT infrastructure that might otherwise lead to a data breach. Netragard’s penetration testing services are delivered in three configurations that enable us to tailor our services to each customer's unique requirements.
Our AWS, Azure, and GCP Cloud Penetration Testing services identify configuration issues that could lead to a data breach. We provide effective methods for remediation to ensure any discovered issues are resolved.
Our IT security advisory and consulting services are designed to facilitate knowledge transfer around how hackers think. This service is customized to provide clients with advice and direction unique to the security of their systems, applications, infrastructures, policies, and documentation.
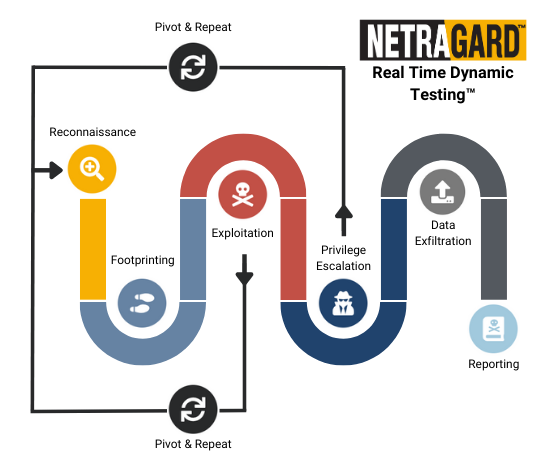
Real Time Dynamic Testing™ is an advanced penetration testing methodology that is unique to Netragard and derived from vulnerability research & exploit development practices.
The methodology is highly extensible and often incorporates components from the OWASP, the OSSTMM, bleeding edge offensive tactics, and more. Real Time Dynamic Testing™ can be delivered entirely without automated vulnerability scanning.
This detailed whitepaper will provide you with insights on how vendors price penetration tests and provide you with 20 questions to better understand the capabilities of a penetration testing partner.

What better way is there to serve as a trusted resource for clients than to provide valuable resources? Keep up to date with our thoughts » More Posts