Since you’re reading this article today, you may not necessarily be the most outdoorsy type. So, rather than being bit by mosquitos and getting a sunburn – let’s celebrate today in the cyber wilderness, where “hunting” takes on a new meaning.
In this virtual landscape, threat hunters are the ones tagging game. Armed with cutting-edge tools, they search through networks and systems rather than mountains and valleys. Their role involves scrutinizing data and identifying anomalies, akin to tracking signs in the wild, but in the world of zeros and ones.
Hunters and fishermen are known for catching their prey in the outdoors. In the digital realm, however, “phishing” is the primary means of predation and has a whole new meaning. It represents the efforts of malicious attackers who use deceptive tactics to trick victims into revealing private information. These attackers rely on setting hooks in the mind, not in the mouth.
Typically, one doesn’t wear camo when fishing, but when attackers engage in phishing campaigns – they tend to hide in the shadows and can be very difficult to notice…
Teach a Man to Phish
A year and a handful of months ago is when I discovered the Darknet Diaries podcast. I was obsessed and listened to every available episode within just a couple of months. An episode I found particularly fascinating was EP 121: Ed:
JACK: Sometimes I think I’m just, like, one click away from a total catastrophe. The perfectly crafted email at the perfect time can cause major damage. Just look at what happened to Barbara Corcoran. She’s the judge on the TV show Shark Tank. Here’s a clip from CBS This Morning:
CBS HOST: I’ve got a very important warning of a financial scam here. One of the stars of the reality show Shark Tank says she was a victim of – they’re calling it a phishing scam, but really, it’s a digital con job. Barbara Corcoran: this is what happened. Last week her bookkeeper received an email about an invoice, and it appeared to be from Corcoran’s assistant, a trusted source, approving payment for a real estate renovation.
JACK: So her bookkeeper was told to send about $400,000 to someone regarding some real estate expense. The email looked like it came from Barbara’s assistant, a trusted person, and since Barbara was a real estate investor, this looked like a typical money transfer. So her bookkeeper wired the money to this person, and it turns out it was all just a phishing email. Barbara lost $400,000 because of a single spoofed email. This hack wasn’t technical. It was manipulating a person, not a machine or a computer. I fear that we may always be vulnerable to this type of attack. We can’t update the firmware in our brain. Yes, we can be educated on how to spot this type of thing and avoid it, but even some of the most educated people on phishing attacks and social engineering have fallen victim to phishing emails. I think people may have bigger vulnerabilities than computers.
At the time, with no cybersecurity background, it seemed ridiculous that huge financial losses could be attributed to something as simple as a phishing attack. No one with even an ounce of awareness would actually fall victim to one of those Prince of Nigeria scam emails… right?
“But what if it was more sophisticated and tailored to an individual victim?” – Me, to myself, circa back then.
The First Baited Hook
My curiosity had peaked. I had to try my hand at it. In hindsight, it was cruel and to this day I regret it, but I tested my capability on my girlfriend. I already knew what could be discovered through publicly available information: she’s a hairdresser that uses certain high-end brands of product. I had my attack vector:
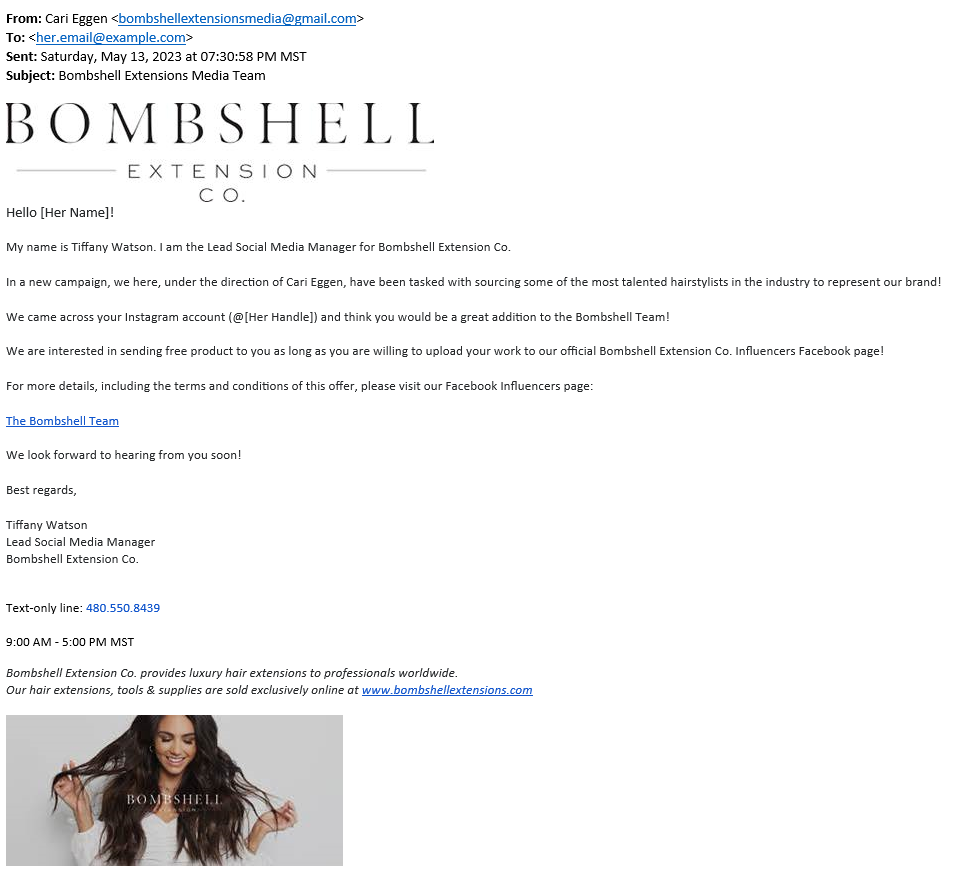
The First Catch & Remorseful Release
I notified her that I was going to send a phishing email and would like her to “grade” me on how believable it was. A+ for “I would fall for it” and an F for “This is obvious.” She arrived at the house shortly after. From my office, I shouted asking her if she had received it yet.
“Not yet. But you’ll never guess what email I did get!”
The hyperlink ‘The Bombshell Team’ would have landed her on a fake Facebook login provided by the PyPhisher tool that I had cloned from Github.
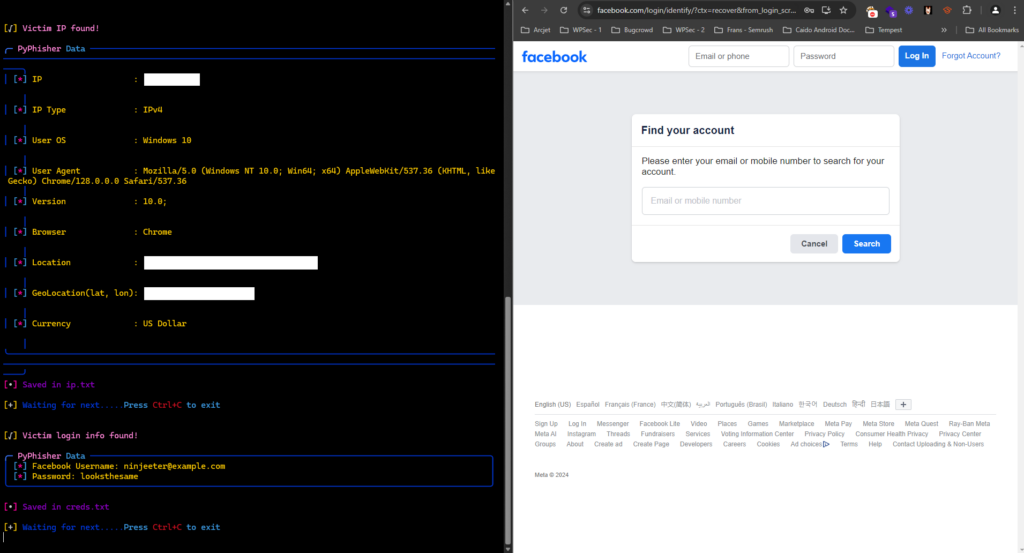
However, I felt so bad that I immediately admitted it was my work and that I regretted using her as a test subject. Had I not intervened, her credentials would have been captured as soon as she submitted them to the clone.
“A+”
Hook, Line, and Sinker
Humans serve as a much easier attack vector for malicious attackers when compared to the hardened systems and robust security teams seen in large organizations – bypassing the defenses of someone’s mind is usually the path of least resistance when it comes to cyber-attacks.
Open-Source Intelligence (OSINT) gathering is the practice of collecting information about a target using publicly available sources. The names of relatives/coworkers, recent life events, personal interests, where the target is located, projects they are involved in, or duties they are responsible for can all aid threat actors in social engineering engagements. In today’s digital landscape, many underestimate the security risks of public exposure online. While some eagerly seek internet fame, even those maintaining a low-profile face potential threats. Advanced tools now exist that can uncover personal information with alarming ease. This combination of widespread desire for visibility and sophisticated data-mining capabilities creates a precarious situation for online privacy and personal security.
- Background search services, such as TruePeopleSearch, aggregate a wide variety of publicly available data associated with a target. All an attacker needs to know is a target’s name, phone number, or email address.
- Photographs including a target can be analyzed by tools such as GeoSpy in order to determine the location of the image. Advanced facial recognition software such as PimEyes can also return photos of a target on the internet that they were completely unaware of.
- Court records can also be parsed and are available via websites such as juryrecords.
- Data dumps obtained through hacker forums such as BreachForums can provide sensitive information on a target. A target’s address, phone number, payment details, and even their social security number may be included in a data breach.
Social engineering is a psychological attack used to manipulate or deceive a person into giving away sensitive information or compromising security. The “social” aspect of social engineering is leveraging human emotions such as fear, excitement, or establishing a sense of urgency. These campaigns can be bolstered thorough OSINT gathering to make the engagement even more believable.
Phishing is a specific subtype of social engineering which utilizes forms of communication such as emails, text messages, or illegitimate websites as mediums of delivery. There are different types of phishing attacks, though the lines between them can bleed into each other, but all seek to extract sensitive data or install malware:
- Spear Phishing: A spear phishing attack is a highly targeted form of phishing in which malicious attackers perform OSINT gathering on a specific individual or group within an organization in order to craft personalized messages. By leveraging details about the target’s personal or professional life – these attacks are generally more successful as they appear more legitimate. In an analysis of 50 billion emails performed by Barracuda Networks, spear phishing emails amounted to less than 1% of all emails sent but were responsible for 66% of all breaches.
- Vishing: Video or phone calls are utilized for vishing attacks. Recently, a multinational company based in China became a victim of a vishing attack. Attackers used deepfake technology to deliver a fake video conference call to an employee. In the video, digitally rendered coworkers (including what appeared to be the Chief Financial Officer) requested that the targeted employee make a fund transfer. The call was convincing enough that $25.6 million dollars was sent to the attacker’s account!
There is also deepfake software, such as ElevenLabs, that can clone someone’s voice or provide realistic text-to-speech audio.
- Business Email Compromise (BEC): In a BEC attack, cybercriminals send deceptive emails with the objective of coaxing a business or individual into making a money transfer to an account under the attacker’s control. This variant of attack differs from other types in that it does not utilize malware, malicious links, or attachments. According to a public service announcement by the FBI – between October 2013 and December 2022, over $50 billion has been lost due to BEC scams.
In IBM’s latest annual X-Force Threat Intelligence Index report, which monitors over 150 billion security events per year across more than 130 countries, several key statistics highlight the frequency and severity of phishing attacks:
- Phishing comprised 30% of all remediated incidents.
- Artificial intelligence software, such as FraudGPT, can generate a deceptive phishing attack in ~5 minutes.
- 92% of organizations were victims of a successful phishing attack in their Microsoft 365 environment in 2023.
- 25% of phishing attacks bypassed Microsoft’s security mechanisms in Microsoft 365.
The Tacklebox
There are numerous tools available for phishing. These tools enable attackers to craft highly convincing scams.
Flipper Zero
Flipper Zero is a small receiver-transmitter capable of hosting fake Wi-Fi access points with the Wi-Fi Devboard attachment and custom firmware such as Xtreme.
The developer board is equipped with an ESP32-S2 series module that enables Wi-Fi capabilities in the 2.4GHz band of the electromagnetic spectrum. The application allows you to arbitrarily name the SSID and serve basic HTML pages that are stored on the device’s SD card.
To demonstrate, I am using an HTML file that appears to be a captive portal for Delta Airlines. You may already be familiar with captive portals, they’re common when using Wi-Fi offered by businesses (just don’t do that, use a password protected hotspot instead).
In fact, masquerading as free-to-use Wi-Fi within a public setting such as a hotel, cafe, library, or airport is a tactic used by malicious attackers. The SSID is named “FREE_WIFI”:
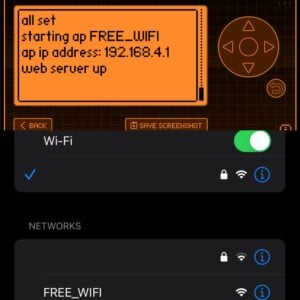
As soon as someone connects to the “FREE_WIFI” access point – the captive portal is presented.

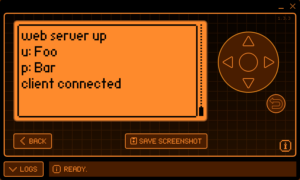
Once a victim submits their credentials to the form, radio frequency signals transmit them as binary data by applying frequency key shifting to a carrier wave. These signals are processed by the Flipper Zero to be displayed as plaintext.
Evilginx
Evilginx is a man-in-the-middle (MitM)/adversary-in-the-middle (AitM) reverse proxy that acts as an intermediary between a client and a server. Any data sent between the two is recorded before it is passed along to the intended recipient. In addition to capturing victim credentials, Evilginx also intercepts and stores session tokens – meaning it can bypass certain types of Multi-Factor Authentication (MFA).
Evilginx uses webpage templates called “phishlets.” A phishlet is a .yaml configuration file that proxies a legitimate website via an illegitimate one. When a phishlet is enabled, Evilginx will automatically request a Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificate from Let’s Encrypt – avoiding any browser warning about an insecure website and allow an attacker to arbitrarily add subdomains to the base registered domain.
Once these phishlets have been enabled, Evilginx will generate an associated link referred to as a “lure” that can then be distributed to targets.
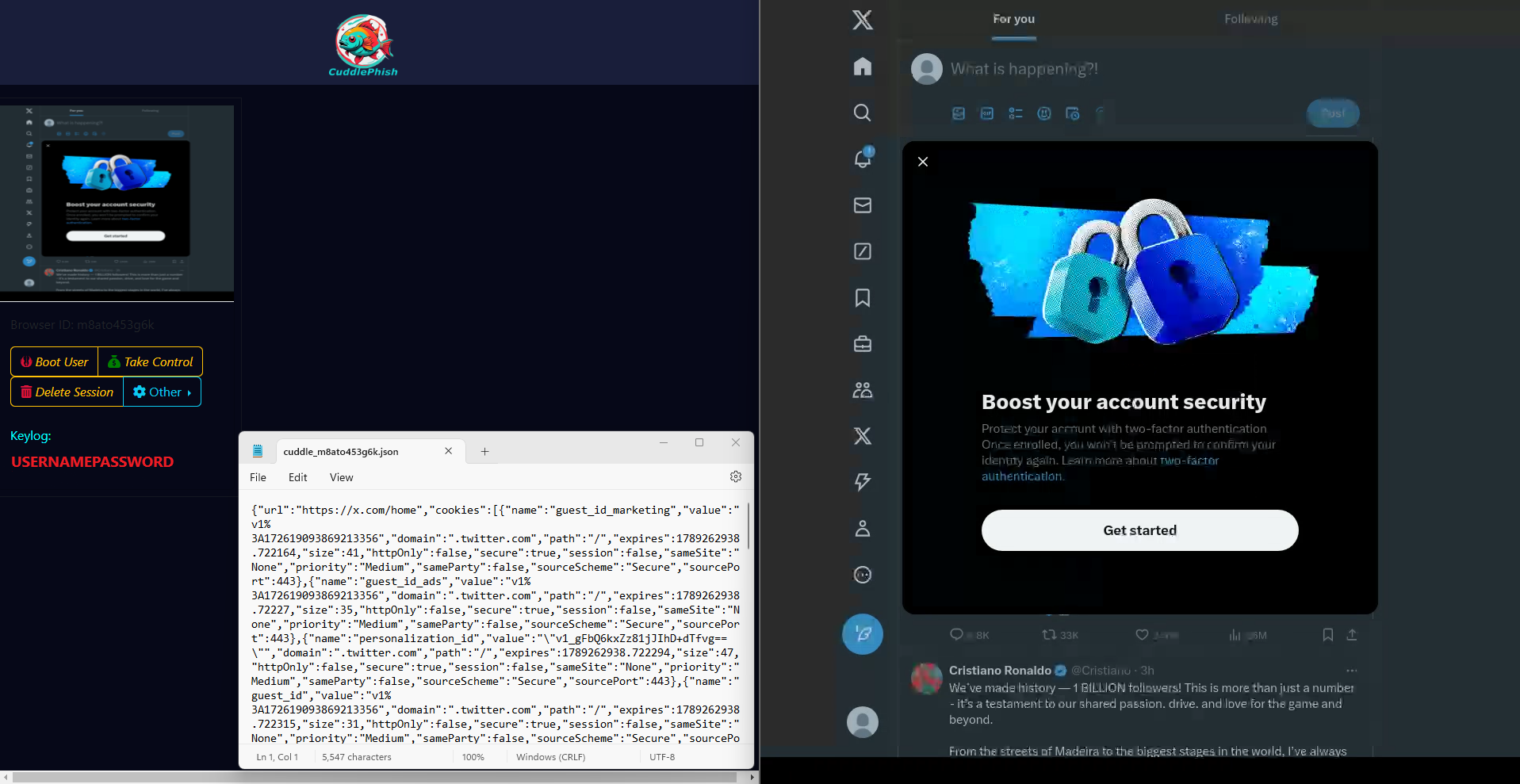
CuddlePhish
CuddlePhish is a browser-in-the-middle (BitM) tool. BitMs utilize the Web Real-Time Communication (WebRTC) API. This technology lets web applications capture and stream video between browsers. The following is a snippet from Mozilla documentation on WebRTC:
WebRTC serves multiple purposes; together with the Media Capture and Streams API, they provide powerful multimedia capabilities to the Web, including support for audio and video conferencing, file exchange, screen sharing, identity management, and interfacing with legacy telephone systems including support for sending DTMF (touch-tone dialing) signals. Connections between peers can be made without requiring any special drivers or plug-ins, and can often be made without any intermediary servers.
CuddlePhish casts a net to take advantage of targets using Screen sharing capabilities. Once victims are convinced to click on a link:
- A phishing site will be presented with a page in their browser that is just a screen share video feed of the attacker’s browser.
- Any browser events such as mouse movements or keyboard key strokes performed by the victim are listened for using the addEventListener() method. Victim input and actions, in what they believe to be their browser, are then sent to the CuddlePhish server via a WebSockets connection.
- These events are then replicated in the actual browser window of the attacker using Puppeteer. Puppeteer uses the DevTools protocol in order to automate browser activity and tasks. By using different objects and methods provided by Puppeteer, such as the Mouse and Keyboard classes, any victim triggered events will be mirrored to the attacker’s browser. Because of this, to the victim that is only watching a video feed of the attacker’s browser, it appears as if they’re interacting with the actual page themselves.
Basically, you can conceptualize CuddlePhish as a keylogger hiding in plain sight.
Your Favorite Holiday
On this National Fishing and Hunting Day, we’ve explored a different kind of wilderness – the digital landscape. Just as skilled hunters and anglers use specialized tools and techniques in the great outdoors, threat actors employ sophisticated methods in their online pursuits. Their social engineering and phishing campaigns are like well-camouflaged traps, blending seamlessly into our digital environment. As we conclude our cyber expedition, you can proudly say you’ve celebrated this day in a unique way, “hunting” for knowledge in the vast online ecosystem. Now it’s time to “reel in” your thoughts and relax, having navigated the challenges of our modern, digital wilderness.






