Home → Cloud Penetration Testing Services
Secure your cloud infrastructure with an in-depth analysis of your cloud configuration to pinpoint overprivileged accounts, unintended access points, and identify the path to compromise attackers may use to exploit your systems and data.

Netragard will test your cloud environments for misconfigurations that hackers may exploit to compromise your systems and data. This process starts by analyzing the cloud subscription in order to understand which services are in use and how they are configured. As services are identified, we conduct a deeper inspection to identify the potential risks and improvements. Following the completion of the assessment, we will provide you with a report detailing recommendations that are in line with best practices to help prioritize findings.
We have expertise in the following cloud service provider networks:
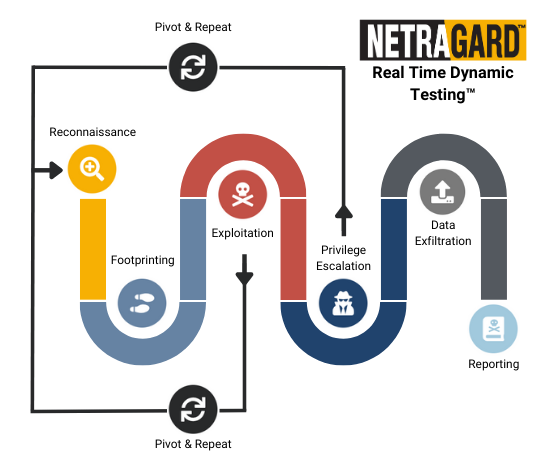
Real Time Dynamic Testing™ is an advanced penetration testing methodology that is unique to Netragard and derived from vulnerability research & exploit development practices.
The methodology is highly extensible and often incorporates components from the OWASP, the OSSTMM, bleeding edge offensive tactics, and more. Real Time Dynamic Testing™ can be delivered entirely without automated vulnerability scanning.
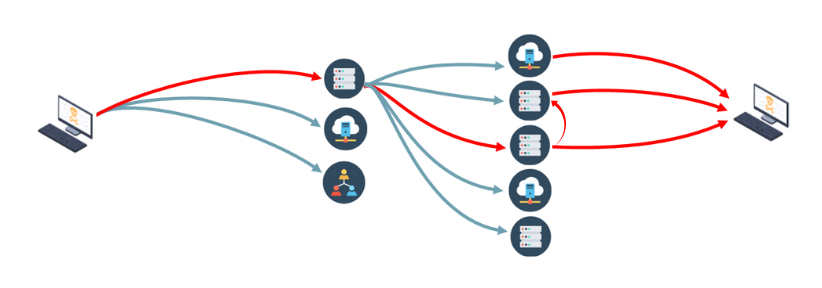
The Path to Compromise is the path that an attacker takes to move laterally and/or vertically from an initial point of breach to areas where sensitive data can be accessed.
Understanding the Path to Compromise enables organizations to deploy effective defenses that detect and prevent active breaches from becoming damaging.